|
|
|
Last revised October 30, 2017
The
contents of this website, the links contained therein directly and
indirectly, and the contents of the said links, are copyrighted.
They are provided exclusively for
non-profit educational use by the students currently enrolled in this
course and for the duration of this semester. No other use is
allowed
without permission from the copyright holder or holders. The
Power
Point slides linked from this page have been adopted for this course
and its students based on the copyrighted original slides that come
with the textbook available at textbook's website http://wps.prenhall.com/bp_beekman_tomtech_8/. All the corrections,
additions, and modifications to the original slides are subject to
copyright(s) by the professor for this course and/or third parties, but
not by the textbook publisher, whether indicated as such or not. No
videotaping or recording without professor's prior permission is
allowed in class.
Lecture Notes
Click here to go to
the current Notes.
Quick
Links
Week 1
Appendix
A
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Appendix.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
A propos flash (USB) memory retention ...

Weeks of flash
memory retention for Client typical use in function of "power-on
temperature" and "power-off temperature", both in centidegrees ( oCelsius ):

The above data are quoted from http://www.anandtech.com/tag/storage.
Week 2
Chapter 1
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap1.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Notebook PC diagram

http://www.vaughns-1-pagers.com/computer/pc-block-diagram.htm
http://www.hitequest.com/Kiss/computer_arch.htm
System unit. a.k.a.
motherboard (with the acronyms explained)
http://computer.howstuffworks.com/motherboard1.htm
Who invented today's computer?
As
I said in class, many people are given credit for the invention of a
computer, but one needs to take these kinds of claims with a grain of
salt (a dose of skepticism, if you will). Fact that there is a
consensus of some kind regarding who was "the first that ..." doesn't
mean much in itself. For any such claim, there is a number of questions
one may wish to answer before awarding the actual credit for the
invention of computer.
1. What is the evidence that the invention was actually made at the
time it was claimed to be invented?
2. Does there still exist an actual device built at that time that
shows it was (or still is) functional?
3. Did said device perform as desired or was it just unfinished,
however interesting, experiment?
4.
If the device does not exist today then does there exist a proof of its
earlier existence and functionality? For instance, does there exist a
documented evidence of actual computations made by that device, or was
it just an idea on a paper that did not materialize, or an inconclusive
experiment?
5. If s sequence of improvements were made by the
inventor to his original idea then when was the first time when the
device was able to to perform actual computations as required?
6. (This is, perhaps,
the most important question to ask.)
Did the invention in question open a way for future progress in
technology that led to today's computers or was it abandoned and did
not result in further development?
It appears that many inventions acclaimed as "computers" would not pass
the muster of the above questioning.
ENIAC was unquestionably an electronic, digital, programmable computer
from which today's computers evolved.
According
to existing evidence, Colossus by a team headed by Alan Turing (Tommy
Flowers was the engineer on that team that designed Colossus) was
unquestionably a computer in today's understanding of this word
(electronic, digital, and programmable) that was fully functional (not
just an idea or interesting experiment, whether leading to further
discoveries or not) at the time it was built.
As to earlier
inventions, I remain skeptical. Not that they weren't brilliant or did
not contribute to the body of knowledge that laid foundations for
computer science and technological progress, but there is just not
enough hard evidence to prove that a fully functional computer (in
today's sense of this word) was actually built before 1943.
For
instance, Babbage's "Analytical engine" (entirely mechanical
construction) was built only partially and Babbage was never able to
make it actually function.
Zuse's Z1, Z2, and Z3 computing
devices were destroyed during the WWII and there seem to be no hard
evidence that they were fully functional, although the Internet abounds
with enthusiastic (albeit unsupported by contemporary evidence) claims
of their computing capabilities. I am not aware of record of actual and
useful computations that they performed, as many enthusiasts seem to
claim. None of these devices were "electronic", that is, they
were based on electromechanical relays. And the Zuse's project was
abandoned due to a lack of interest from the German authorities during
the WWII. I realize that it's fashionable (in some circles) to give
credit to Zuse for the invention of contemporary computer, but unlike
Colossus machines, his Z1, Z2, and Z3 do not quite fit into
genealogical lineage of today's computers (just like the Neanderthal
men were not ancestors of today's Homo
Sapiens
despite numerous similarities between the two species). It's worth
noting that Zuse himself appeared unwilling to accept the credit for
the invention of computer.
Atanasoff-Berry computer was not
programmable and was able to perform only some specific calculations
(was used to solve systems of linear equations). The project was
abandoned.
So, how did we get from there to here? Vacuum tubes
(on which Colossus was built) in computers were replaced by transistors
very much the same way how they were replaced in consumer electronics
(radios and TVs). Then millions of transistors were packed on single
integrated circuits, and voila! Quite
a
lot
of
architectural
and
technological
improvements were made in the
process, but the main ideas (not surprisingly championed by Allan
Turing) remained almost the same.
Colossus project died due to
security requirements (it was a secret military project) without
offspring, although it and his head, Allan Turing, had tremendous
impact on computer science that was about to emerge. So, it appears, that ENIAC is the
earliest real ancestor of electronic, digital, programmable computers
that we use today.
Week 3
Chapter
2
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap2.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Link for Chapter 2
Typical instructions for
Intel microprocessor:
http://www.jegerlehner.ch/intel/opcode.html
Week 4
Chapter
3
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap3.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Week 5
Chapter
4
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap4.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Week 6
Chapter
5
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap5.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Week 7
Chapter
6
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap6.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Week 8
Chapter 7
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap7.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Week 9
Chapter 8
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap8.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
The relationship
between wavelength and frequency.
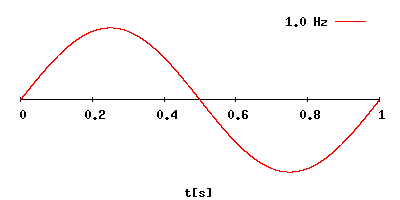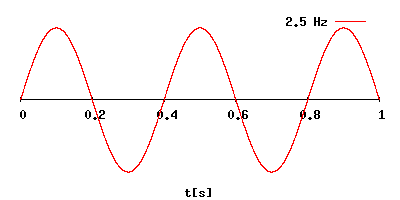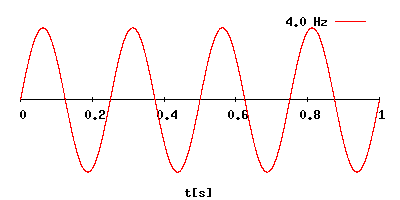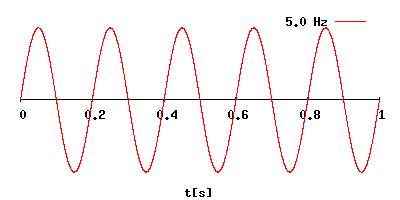
The frequency is
displayed in the upper right corner of the above picture.
The wave length is
visualized on x-axis.
If the frequency is in
Hertzs (Hz) then 1 on x-axis equals to 300,000 km (or 186,000 miles).
If the frequency is in
kiloHerzs (KHz) then 1 on x-axix equals to 300 km.
If the frequency is in
megaHerzs (MHz) then 1 on x-axix equals to 300 m.
If the frequency is in
gigaHerzs (GHz) then 1 on x-axix equals to 0.3 m (or about 1 ft).
If the frequency is in
teraHerzs (THz) then 1 on x-axix equals to 0.3 mm.
The distance of 300,000 km (or 186,000 miles) is how far the light will travel in vacuum in 1 second.
1 light-year is the
distance that the light will travel in vacuum in one year. It is
approx. 5.9 trillion miles (or 9.5 trillion km).
Electromagnetic
waves
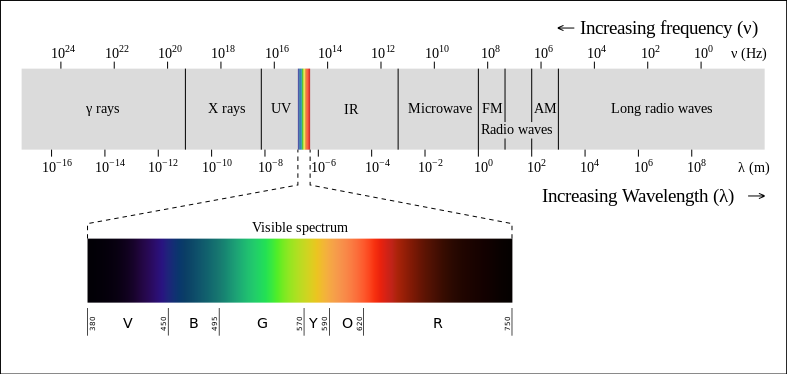
IR means infrared wave. On the above
picture it is to the right ot red. Infra
means (in Latin) under and
indicates that it has lower frequency than red light.
UV means ultraviolet wave. On the above picture it is to the left ot
violet. Ultra means (in Latin) beyond
and indicates that it has higher frequency than violet light.
1 m (meter) is approximately 3.3 feet.
1/1,000 m (or 10-3
m) is equal to 1 mm (milimeter)
1/1,000,000 m (or 10-6
m) is equal to 1 µm (micrometer)
1/1,000,000,000 m (or 10-9
m) is equal to 1 nm (nanometer)
Week 10
Chapter 9
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap9.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Here is a link to glossary
of
acronyms:
http://www.almcom.net/Glossary/glossary_A.html
Digital Object Identifier (DOI) for
documents
posted on the Internet is
an alternative to Universal Resource Locator (URL). Unlike URL, DOI is
permanent in that it does not change when the document in question is
moved from one page or website to another.
DOI is often used in Internet-based literature references, as - for
instance - on this Wikipedia page:
http://en.wikipedia.org/wiki/Heap_(data_structure)#cite_note-5
A translator of DOI
on the current URL may be found here:
http://dx.doi.org/
For instance, this DOI
10.3233/FI-2012-751

resolves to this URL:
http://content.iospress.com/articles/fundamenta-informaticae/fi120-1-05
Week 11 and 12
(Skip the entire Chapter 10)
The
scantron
test will cover material contained and linked from herein.
Intellectual Property, Its Protection, and Preemption
PowerPoint
slides
used in class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap10.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
and
http://csc.csudh.edu/suchenek/CSC101/Slides/OffshoringGoodOrBad.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Reading:
http://csc.csudh.edu/suchenek/Papers/Computers_and_Society.htm
U.S.
Constitution, Article 1 Section 8 Para 8
"To promote the Progress of Science and useful Arts, by securing for
limited Times to Authors and Inventors the exclusive Right to
their respective Writings and Discoveries;"
http://constitutionus.com/
Fair use
exception from the copyright law
https://www.copyright.gov/title17/92chap1.html#107
ACM Code of Ethics
1.5 Honor property rights including copyrights and patent.
Violation of copyrights, patents, trade
secrets and the terms of license agreements is prohibited by law
in most circumstances. Even when software is not so protected, such violations are contrary to
professional behavior. Copies of software should be made only
with proper authorization. Unauthorized duplication
of materials must not be condoned.
http://www.acm.org/about/code-of-ethics
Scheme of public key
encryption

Source: http://cxf.apache.org/docs/ws-security.html
How Encryption Works
http://computer.howstuffworks.com/encryption3.htm
Public-Key Cryptography
http://www.aspencrypt.com/crypto101_public.html
Optional
reading
-
highly recommended
George Orwell "1984"
The book: (optional)
http://www.mondopolitico.com/library/1984/1984.htm
The movie - trailer
(Introduction)
http://www.youtube.com/watch?v=XMrcJFrUgTM
The
movie:
(optional)
http://www.ebaumsworld.com/video/watch/81753727/
A
Review
by
Scott
Hughes
http://onlinebookclub.org/1984.php
"Nineteen Eighty-Four
(1984) is a dystopian novel written by the English writer George Orwell
(1903 - 1950). The novel was first published in 1949. The book tells
the story of fictional character Winston Smith and his attempt to rebel
against the totalitarian state in which he lives.
"Nineteen Eighty-Four
remains as one of the most popular and widely read books of all time.
Indeed, the novel has even greatly affected common language and created
new phrases, words, and idioms. For example, the commonplace term 'big
brother' comes from Nineteen Eighty-Four.
"The impact of Nineteen
Eighty-Four is not surprising, because the well-written novel amazingly
predicts a frightening future with shocking accuracy. In contemporary
society, the novel can frighten readers even more, since the readers
can actually see how much of the Orwell's warnings have come to pass.
"With Nineteen
Eighty-Four, Orwell depicts a - at his time - futuristic totalitarian
government that uses fear, deception, and manipulation to force total
obedience and conformity. The totalitarian government wages perpetual
wars to keep the people in fear, thus excusing the government from its
failures and oppression. The totalitarian government uses constant
surveillance [based on advanced information technology that is
available today] and "thought policing" to stifle rebellion. The people
live in constant reminder that they have no freedom, with signs that
say, "BIG BROTHER IS WATCHING YOU."
Week 13
Chapter
12
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap12.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Links
from the slides: (for information only - not covered by the test):
Information Technology Curricula 2017
Curriculum Guidelines for Undergraduate
Degree Programs in Information Technology
"Definition of the Information Technology Academic Discipline
Information Technology is
the study of systemic approaches to select, develop, apply, integrate,
and administer secure computing technologies to enable users to
accomplish their personal, organizational, and societal goals."
http://www.acm.org/binaries/content/assets/education/it2017.pdf
QUANTUM INFORMATION
TECHNOLOGY:
Entanglement, Teleportation and Memory
a Joint Program of the Massachusetts Institute of Technology
and Northwestern University
http://www.rle.mit.edu/quantummuri/Shapiro.pdf
Week 14
Chapter
13
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap13.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.

Source:
US Census Bureau
http://www.census.gov/retail/mrts/www/data/pdf/ec_current.pdf
Week 15
Chapter
15
PowerPoint slides used in
class:
http://csc.csudh.edu/suchenek/CSC101/Slides/Chap15ms.pdf
It's a copyrighted
material, so the students in this class can read them but not to copy or distribute
them.
Video "HOW TO RECORD YOUR
OWN MUSIC 101" (24 min.)
to watch after class - there will be 4 questions
on the final from this video, so make sure you watch it form the
begining to the very end:
http://csc.csudh.edu/suchenek/CSC101/Videos/LowerResEtc/HowToRecordMusic_large.m4v
If your connection
is slow then try this lower resolution format: http://csc.csudh.edu/suchenek/CSC101/Videos/LowerResEtc/HowToRecordMusic_medium.m4v
It's a
copyrighted
material, so the students in this class can watch the video but cannot copy, share, or distribute
it.
Weeks of classes in Fall 2017:
week 1: Aug 22, 24
week 2: Aug 29, 31
week 3: Sep 5, 7
week 4: Sep 12, 14
week 5: Sep 19, 21
week 6: Sep 26, 28
week 7: Oct 3, 5
week 8: Oct 10, 12
week 9: Oct 17, 19
week 10: Oct 24, 26
week 11: Sep 31, Nov 2
week 12: Nov 7, 9
week 13: Nov 14, 16
week 14: Nov 21
week 15: Nov 28, 30
week 16: Dec 5
week 17 (final): Dec 7
Note
This page and the entire course
website http://csc.csudh.edu/suchenek/CSC101/ may contain
copyrighted material that is included and/or used for non-profit
educational purposes only, and not for any other purpose, and only for
the duration of the course. Click here
for U.S. Code Tittle 17 Chapter 1 para 107 containing the "fair use" exception for
copyrighted material.
|
|